The Shift from Email to Collaboration Platform Attacks

Introduction
The days of cybercriminals only targeting email are over. Today, 51% of business communication happens outside of email—on tools like Slack, Microsoft Teams, CRM platforms, and Zoom. These tools are fast, trusted, and deeply embedded in how teams collaborate. But that same convenience makes them prime targets. Recent high-profile breaches show attackers are already exploiting them—with potentially devastating consequences.
In this blog, we’ll explore how modern attacks unfold across these platforms, what’s at stake, and how Disso helps you stay ahead of them.
1. Why Collaboration Tools Are Attractive Targets?
Slack has an interesting origin story. It was founded by Stewart Butterfield in 2013, after his gaming start-up failed to take off. The team pivoted to an internal messaging tool they’d built to improve communication — and that became Slack. 3 years later, Microsoft launched Teams, and the COVID-19 pandemic accelerated the rise of video tools like Zoom. These platforms shared one goal: making digital work easier and more connected. As more people adopted them, they became essential, trusted tools — largely because everyone else at work was already using them. They didn’t just support remote work; they helped redefine it.
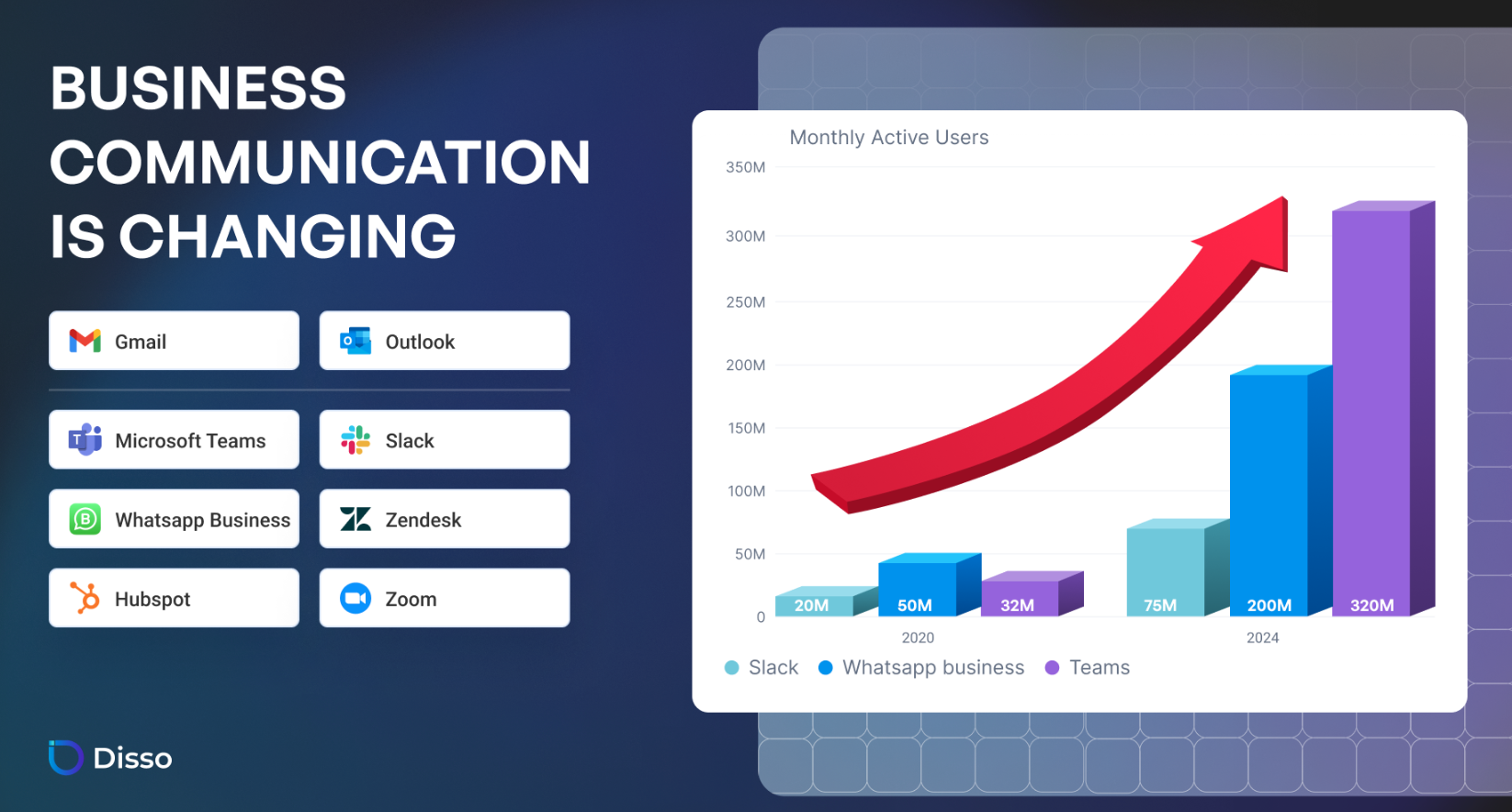
But with their rise came new risks — these tools became prime targets for attackers, for several key reasons:
- Trust in internal communication: Employees tend to trust messages from colleagues. That makes phishing over Slack or Teams far more convincing.
- Short messages, less scrutiny: Most Slack messages are just 20 words long compared to 75–120 words for email—much easier to miss red flags compared to email.
- Constant file and link sharing: HAR files, Excel sheets, PDFs, dashboards—attackers don’t need to “hack” in, they just need to share a file at the right moment.
- Low awareness of phishing in chat: Staff are trained to spot email scams, not Slack DMs. Attackers know this—and take advantage of it.
- Data leakage: Fast-paced chat and SaaS tools make it easy to overshare. In a recent case, Deel allegedly planted an operative in Rippling’s Dublin office who used normal access to search “Deel” across Slack, Salesforce, and Google Drive—quietly collecting sensitive data. No hacking, just trusted access misused.
2. How can they attack your sector?
Let's now dive a bit deeper into how they can attack each of the different sectors.
SaaS
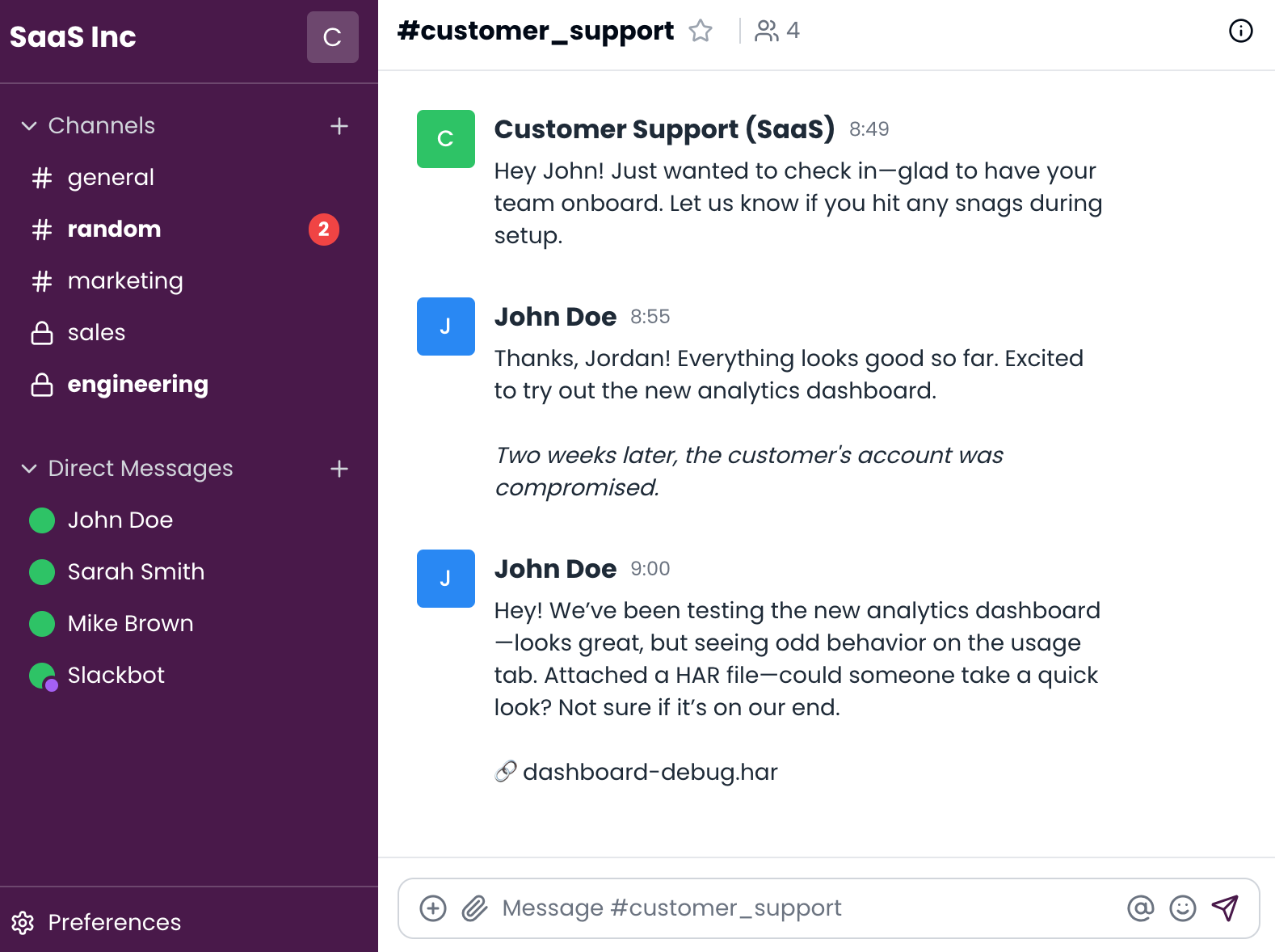
A compromised customer account—breached due to lack of MFA—gains access to a shared Slack channel with your team. The attacker reviews past messages using ChatGPT and spots a recent dashboard rollout. Two weeks later, they exploit the context to share a malicious HAR file. Once opened, it silently harvests internal messages, Jira tickets, and credentials—resulting in a serious breach of trust.
Finance
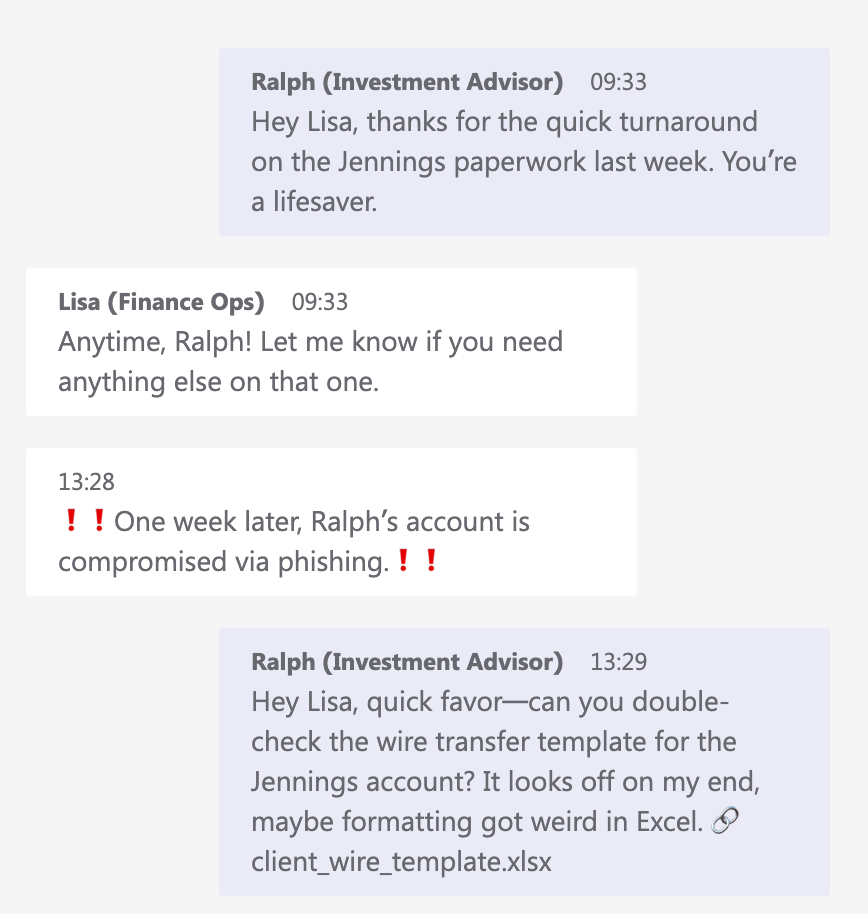
An attacker phishes a finance advisor’s Teams account. Now posing as a trusted internal user, they reference a real wire transfer discussed a week earlier and send a tampered Excel file. Once opened? It harvests client details, shared internal chats, and banking credentials—all from a legitimate-looking Teams message.
3. Does this really happen?
Yes, it does—often and increasingly. You don’t have to take our word for it—here are two well-documented, high-profile cases where collaboration tools became the entry point for serious breaches.
Disney
In July 2024, Disney suffered a major breach. Hackers accessed over 10,000 Slack channels, stealing 1TB+ of data, including 44 million messages and confidential files.
It started when an employee downloaded malware—likely from a game modification—which captured login credentials and access to Disney’s internal password vault. Using those, attackers quietly accessed Slack and exfiltrated sensitive data for months without detection. Eventually, the data was leaked on the dark web.
The breach exposed employee and guest data, internal cloud credentials, unreleased content, and strategic documents. But Slack wasn’t the issue—weak endpoint protection, poor SaaS governance, and no real-time monitoring were. With no layered defenses, what could’ve been contained became a massive data leak.
Uber
In September 2022, Uber was breached when a hacker took over internal systems and announced it publicly in Slack.
The attacker, from the Lapsus$ group, used MFA fatigue and impersonated IT to trick a contractor into sharing credentials. He then accessed Slack, Google Workspace, AWS, and more—posting screenshots to prove it.While no customer data was stolen, the breach caused system shutdowns and internal chaos. The failure wasn’t Slack, but Uber’s lack of protection against social engineering. A single compromised account led to broad internal access—proving how quickly attacks can escalate in modern SaaS environments.
These are multi-billion-dollar companies with massive IT budgets and dedicated security teams. And still—they were breached. So ask yourself: if it can happen to them, why not your team?
The threat doesn’t discriminate by company size—only by opportunity. Any team using Slack, Teams, or a CRM platform without strong controls and monitoring is at risk. And the more collaborative and fast-paced your environment, the easier it is for attackers to blend in.
4. Why Traditional Security Tools Fall Short?
Why can’t third-party tools ensure security even with MFA, Zero Trust models, or procedural controls such as the two-eye principle? The reality is that threat actors have evolved. Just like with email-based attacks, they now exploit human behavior and social engineering rather than brute-force technical flaws. MFA can be bypassed via phishing kits, session hijacking, or MFA fatigue attacks. Similarly, approval-based mechanisms like the two-eye principle are vulnerable if both users are tricked or compromised.
Most third-party tools assume that users are the last line of defense. But your team often isn't trained to recognize advanced threats in real time. And in fast-paced environments, even trained users can’t react quickly enough. Awareness programs help, but they rarely match the speed and sophistication of modern attacks.
5. Closing the gaps in modern security
So then the question arises: what can you do about it? You could rely on your team’s scrutiny—but if you're already investing in email security, why not extend that to platforms like Slack, Microsoft Teams, or Google Workspace? Filtering threats and anomalies across communication channels is essential. Automated detection of suspicious links, impersonation, and unusual activity enables proactive defense—stopping attacks before anything is clicked, shared, or approved.
Disso fills this gap with intelligent threat detection across internal tools, flagging risks and blocking malicious content before it spreads.